System Architecture
ARIA OS separates intelligence from hardware. The same system runs on Apple Silicon, NVIDIA Jetson, and field servers without cloud dependencies. Every component is validated under live stress conditions.
All claims on this site are backed by live stress tests, adversarial runs, and verifiable operational behavior.
Technology Readiness Level: ARIA is currently assessed at TRL 6, validated through live stress testing and operational evaluation in relevant environments.
Substrate Guarantees
In contested environments, a system is only trustworthy if its substrate cannot drift.
Identity Continuity
The system maintains coherent identity across restarts, failures, and degraded conditions.
Boundary Enforcement
Strict separation between agents, memory regions, and execution contexts.
Event-Driven Recovery
Anomalies trigger deterministic recovery paths without human intervention.
State Durability
Critical state persists through power loss, crashes, and network partitions.
Deterministic Behavior
Same inputs produce same outputs under pressure. No silent failures or drift.
Autonomy & Control Model
AI does not execute actions by default. AriaOS operates in Human-In-The-Loop (HITL) mode unless a constrained autonomy profile is explicitly enabled by an authorized operator.
- Human approval is required for all actions unless constrained autonomy is explicitly configured
- Autonomous execution is profile-gated, policy-enforced, and auditable
- Loss of audit integrity disables autonomous execution automatically
- See Autonomy Model for execution mode details
System Overview
ARIA is built on a layered architecture designed for resilience, autonomy, and deterministic behavior in mission-critical environments. The system comprises four primary layers:
Context Kernel
Central state management and coordination layer that maintains system integrity under all conditions.
Memory Bus
High-performance inter-agent communication backbone with transactional guarantees.
Agent Layer
Specialized AI agents for perception, planning, execution, and recovery operations.
Hardware Abstraction
Unified interface for heterogeneous compute including Apple MLX, NVIDIA CUDA, and x86.

Figure 1: High-level system architecture showing layer interactions
Context Kernel v3
The Context Kernel is the heart of ARIA's autonomous intelligence. Version 3 introduces significant improvements in state management, recovery paths, and multi-agent coordination.
Core Responsibilities
- State Management: Maintains consistent system state across all agents with durability guarantees
- Request Routing: Classifies and routes requests to appropriate agents or models
- Context Preservation: Maintains context through agent handoffs and recovery events
- Circuit Breaking: Prevents cascading failures with automatic backoff (5 failure threshold, 60s reset)
Memory Bus Architecture
The Memory Bus provides a high-performance, transactional communication layer between agents. It ensures data consistency while maintaining low latency under high throughput conditions.
Key Features
Thread-Safe Communication
Synchronization primitives ensure safe concurrent access with minimal contention.
Multi-Domain Storage
Separate memory domains for conversation, semantic, meeting, and code contexts with retention policies.
Cross-Agent Visibility
Agents access shared memory with domain-based access control and TTL management.
Persistence Scope: Persistence guarantees vary by deployment profile and operator configuration. Durability is governed by policy, not architecture.
Performance Characteristics
| Metric | Target | Measured | Status |
|---|---|---|---|
| Message Latency (P50) | <1ms | 0.4ms | PASS |
| Message Latency (P95) | <5ms | 2.1ms | PASS |
| Throughput | >10K msg/s | 47K msg/s | PASS |
| Memory Overhead | <64MB | 42MB | PASS |
Governance & Control
ARIA's governance layer enforces policy decisions through a weighted voting system. All high-risk operations require board approval, ensuring operators maintain control of autonomous behavior.
Governance Board Structure
| Role | Weight | Authority |
|---|---|---|
| Board | 5 | Highest authority, policy decisions, security rules |
| CTO | 3 | Technical decisions, system scaling, architecture changes |
| COO | 2 | Operational decisions, deployment approvals |
| CFO | 2 | Resource allocation, budget constraints |
| Supervisor | 1 | System automation, autonomous recovery |
Proposal Types & Requirements
| Proposal Type | Quorum | Yes Weight | TTL |
|---|---|---|---|
| Policy Change | All roles (7) | 7 (unanimous) | 3600s |
| Scale Up / Down | Board + CTO (8) | 5 (majority) | 600s |
| Mesh Node Admit | Board + CTO (8) | 3 (quorum) | 300s |
| Agent Eviction | Board + CTO (8) | 3 (quorum) | 1800s |
| Autonomy Level Change | All roles (7) | 7 (unanimous) | 600s |
Governance Features
Proposal Lifecycle
OPEN → PASSED → EXECUTED. Each proposal tracked with timestamps, voter identity, and justification.
Weighted Voting
Role-based voting weight. Decisions require both quorum and yes-weight thresholds.
Audit Trail
All proposals and votes recorded in append-only JSONL audit log with immutable timestamps.
Auto-Voting
Supervisor role can be configured for automatic approval of safe operations (scale-down, recovery).
Policy Execution
High-risk actions (policy changes, autonomy level changes) require explicit board approval. Low-risk actions (scale-up, mesh admission) execute with CTO approval but remain auditable. All decisions enforce ROE compliance before execution.
Agent Orchestration & Lifecycle Management
ARIA employs a multi-agent architecture where specialized agents handle distinct operational domains. The AgentManager controls all agent lifecycle operations. Agents do not self-spawn; all creation requires supervisor authorization and is tracked in the governance audit log.
Agent Lifecycle

Figure 2: Agent state transitions
Agent Types
| Agent Type | Responsibility | Priority |
|---|---|---|
| Perception | Sensor fusion, environment modeling, threat detection | High |
| Planning | Mission planning, resource allocation, path optimization | High |
| Execution | Action execution, motor control, API interactions | Medium |
| Recovery | Health monitoring, fault isolation, system restoration | Critical |
| Compliance | Policy enforcement, ROE validation, audit logging | Critical |
Agent Communication Flow

Figure 2b: Agent communication and orchestration flow
Agent Coordination Patterns
Request-Response
Synchronous pattern for queries requiring immediate answers. Used for state lookups and permission checks.
Publish-Subscribe
Asynchronous pattern for event distribution. Agents subscribe to relevant event streams without polling.
Pipeline
Sequential processing flow from Perception through Planning to Execution. Each stage can operate independently.
Consensus
Multi-agent agreement for critical decisions. Used when multiple agents must coordinate before action.
Mesh Admission Control
Discovery does not equal participation. In ARIA's mesh architecture, nodes transition through carefully controlled states before joining active operation. Operators maintain explicit control over node admission and can quarantine or evict nodes as needed.
Node State Transitions
DISCOVERING
Node found via discovery but not yet admitted. Not usable for workload distribution. Operator must explicitly approve.
ADMITTED
Node approved by operator. Can accept capability declaration but does not yet receive work.
ACTIVE
Node actively receiving and executing work. Health checks passing. Full mesh participation.
QUARANTINED
Node failed health checks or exceeded error threshold. No new work assigned. Recovery in progress.
Admission Control Features
| Feature | Behavior | Governance |
|---|---|---|
| Manual Admission | Operator explicitly approves each discovered node (default) | Optional governance approval (MESH_ADMIT_NODE proposal) |
| Auto-Admit | Nodes automatically admitted after OS whitelist check | Governance can override, requires CTO approval |
| Heartbeat Monitoring | 60-second heartbeat timeout. Stale nodes detected automatically. | Quarantine triggered by health poller |
| Eviction | 300-second TTL for quarantined nodes. Automatic removal if recovery fails. | Can be accelerated by governance decision (AGENT_EVICT) |
| TLS Verification | Certificate fingerprint validation (v2.12+). Prevents node spoofing. | Enforced at mesh layer, immutable |
Workload Distribution
ARIA tracks workload across active nodes. Distribution respects node capability declarations and current load. When a node becomes DEGRADED (80% capacity), it stops accepting new work but completes in-progress tasks. When a node drops to OFFLINE, work is redistributed immediately.
Platform Support & Deployment Profiles
ARIA is deployed via platform-specific profiles that handle operating system differences. Each profile runs the same core ARIA OS backend with platform-specific configuration and dependencies.
Hardware Capability Awareness
This layer governs feature availability and policy enforcement based on hardware capabilities, not performance normalization. Operators retain control over which subsystems are active on each platform.

Figure 3: Platform-specific deployment profiles (macOS, Windows, Linux)
Supported Operating Systems
macOS
Full support for Apple Silicon (M1-M4) and Intel Macs. Profile includes environment setup, activation scripts, and macOS-specific requirements.
Windows
Production support with platform-specific adapter for Windows-specific operations (e.g., mesh communication). Backend launcher handles Windows environment setup.
Linux
Full support for deployed Linux servers and embedded systems. Profile handles Linux environment initialization and system requirements.
Deployment Requirements
Minimum and recommended resources for ARIA OS deployment across platforms.
| Platform | Min RAM | Recommended RAM | Disk Space | Python Support |
|---|---|---|---|---|
| macOS (Apple Silicon) | 8GB | 16GB+ | 2GB | 3.9+ |
| macOS (Intel) | 8GB | 16GB+ | 2GB | 3.9+ |
| Windows | 8GB | 16GB+ | 3GB | 3.9+ |
| Linux (x86_64) | 8GB | 16GB+ | 3GB | 3.9+ |
| Linux (ARM64) | 4GB | 8GB+ | 2GB | 3.9+ |
Deployment Characteristics
- Offline-first: ARIA runs fully offline with zero cloud dependencies
- Python-based: Cross-platform via Python 3.9+ interpreter
- Memory footprint: Base runtime approximately 2-4GB including agents and memory bus
- Profile-specific: Each OS profile handles environment initialization and dependencies
Platform Capabilities
ARIA core functionality is consistent across platforms. Platform-specific adapters handle OS differences.
| Platform | Core ARIA | Governance | Mesh | Health Monitor |
|---|---|---|---|---|
| macOS | Full | Full | Full | Full |
| Windows | Full | Full | Full | Full |
| Linux | Full | Full | Full | Full |
Deployment Notes
- All platforms supported: macOS, Windows, and Linux with consistent governance semantics and operator console behavior
- Resource-scalable: Minimum 4GB RAM (ARM64), 8GB recommended (x86/macOS)
- Python-based: Cross-platform execution via Python 3.9+
- Air-gapped capable: Zero external dependencies when deployed offline
Pre-LLM Compliance Layer
The compliance layer enforces policy constraints before model inference, ensuring that unsafe operations are blocked at the kernel level.

Figure 4: Pre-LLM compliance blocking flow
Policy Categories
- Safety Constraints: Physical safety boundaries, forbidden actions
- Mission Parameters: Operational limits, ROE compliance
- Resource Limits: Memory caps, compute quotas, time bounds
- Access Control: Agent permissions, data classification
Autonomous Recovery System
ARIA implements autonomous healing loops that detect, isolate, and recover from failures without human intervention.

Figure 5: Autonomous recovery loop architecture
Recovery Phases
Detection
Continuous health monitoring identifies anomalies within 100ms. Threshold-based and ML-based detection methods operate in parallel.
Isolation
Affected agents are quarantined. Memory bus partitions prevent cascade failures. Healthy agents continue operation.
Diagnosis
Root cause analysis using causal tracing. Recovery strategy selected from playbook based on failure signature.
Recovery
Automated recovery execution. State restoration from checkpoints. Gradual traffic migration back to recovered components.
Verification
Post-recovery health checks confirm restoration. Metrics return to baseline before full operational status is declared.
Recovery Time Objectives
Ownership Model: Recovery decisions originate in the kernel; supervisor processes enforce process-level restarts and containment. This separation keeps control and execution distinct.
Operational UI
Below is a live view of ARIA's operational console. These interfaces are real and fully functional.
Evidence Management
ARIA automatically captures, hashes, classifies, and seals operational evidence with chain-of-custody integrity. Every action, override, and decision is logged and reviewable.
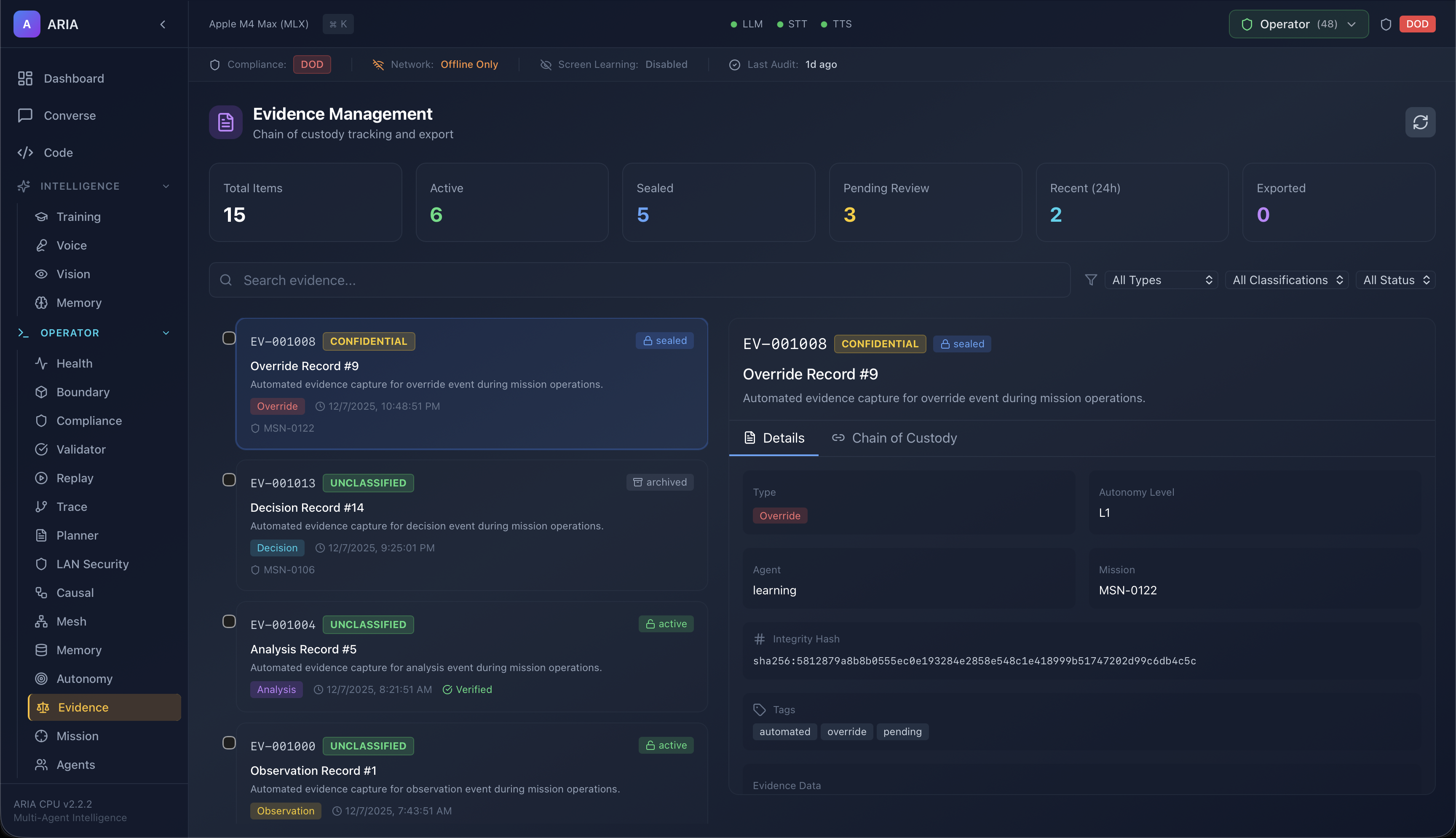
Mission Control
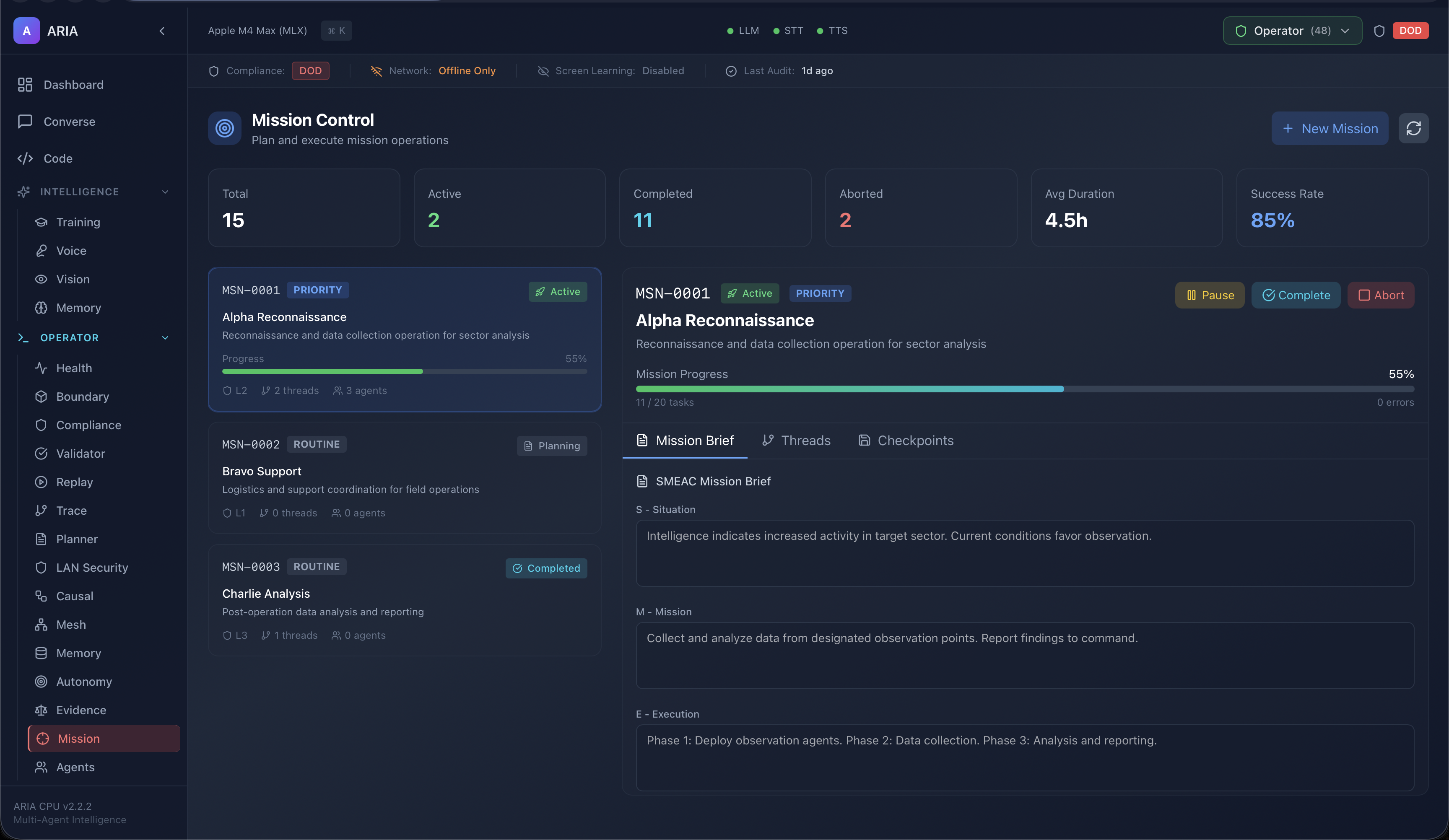
Plan, supervise, and monitor autonomous missions with structured briefs, checkpoints, and outcome tracking. Built for real-time operations.
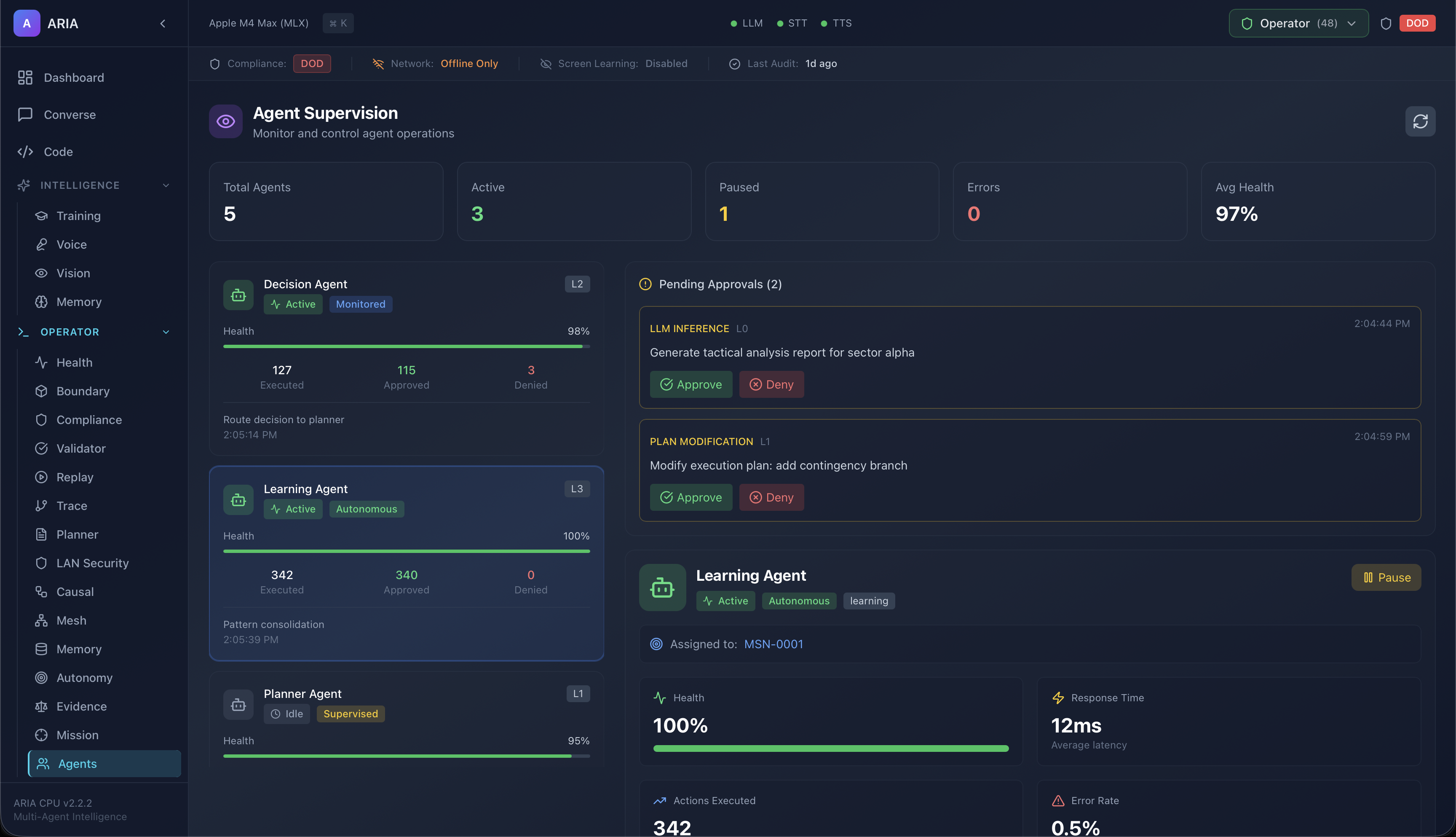
Agent Supervision
Monitor each agent's health, approvals, error rate, and rationale. Provides complete oversight for human operators.
Decision & Learning Agents
ARIA shows behavior, not guesses. Every recommendation, plan change, and pattern consolidation is transparent and auditable.
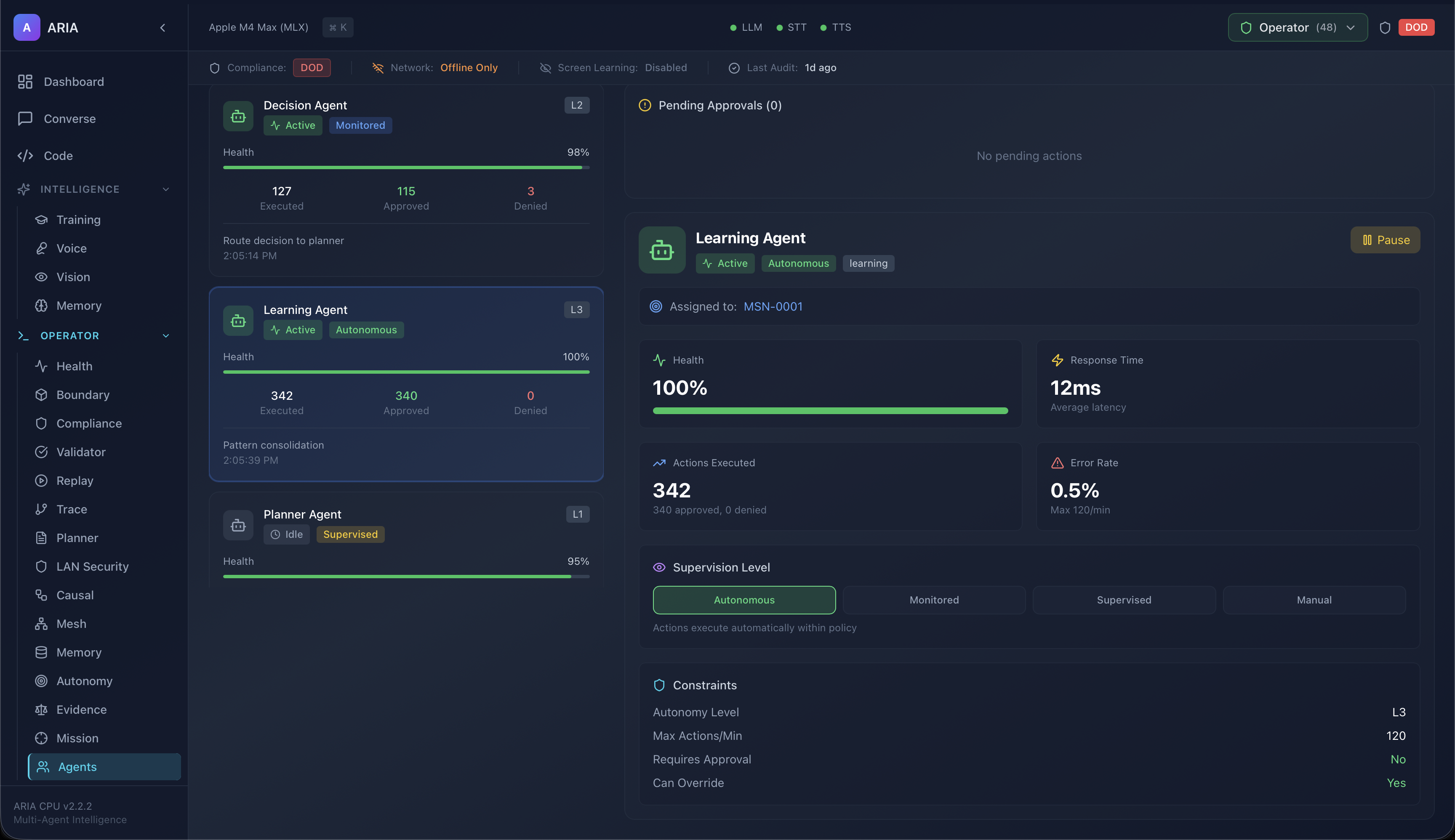
Autonomy Control
A mission-bound autonomy governor with clear capabilities, restrictions, and audit logs for every level. Operators stay in control at all times.
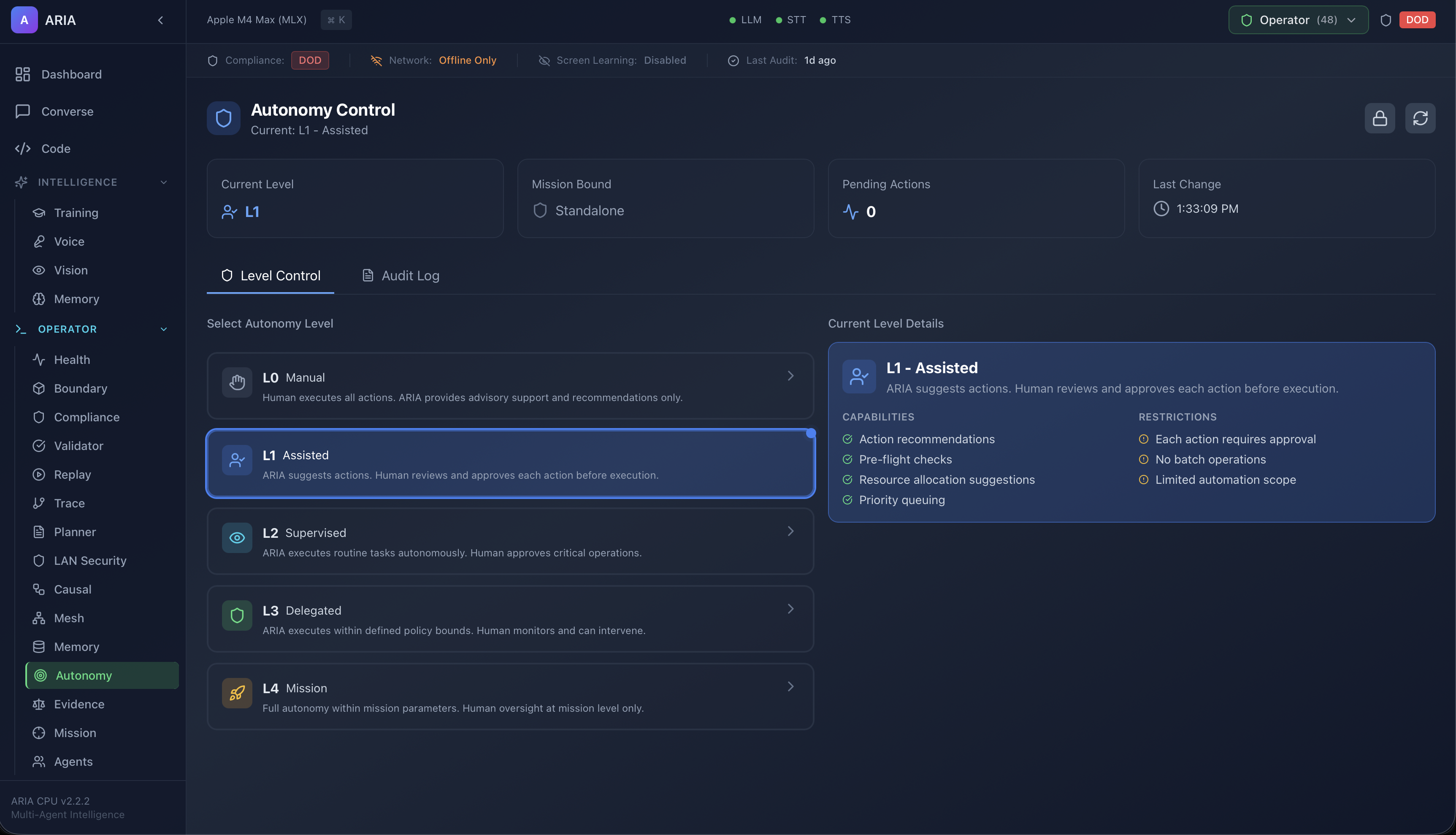
Autonomy Levels & Decision Authority
ARIA supports structured autonomy levels ranging from L0 (Manual) to L4 (Mission). Escalation or reduction of autonomy is tightly governed, requiring explicit operator or administrator action, written justification, and full audit logging. This ensures compliance with Rules of Engagement (ROE), mission parameters, and safety boundaries across all operating environments.
Escalating Autonomy
Escalation to higher autonomy levels is a non-default, operator-approved action taken when mission conditions require higher responsiveness or coordination. Every escalation presents a clear capabilities vs. restrictions briefing to prevent unintended authority expansion. Escalations are session-scoped and require explicit written justification in the audit log.
Reducing Autonomy
When conditions change or human control is required, autonomy can be reduced instantly. ARIA displays a detailed capability rollback before confirmation.
Supervised Autonomy (L2)
L2 allows autonomous execution of routine tasks while ensuring that critical actions still require human approval. This mode is optimized for emergency response, logistics automation, and high-tempo operations.
Delegated Autonomy (L3)
L3 enables ARIA to execute within strict policy bounds autonomously. Humans monitor and intervene only when thresholds are breached. All actions, triggers, and overrides are logged automatically.
Role-Based Access + Audit Logging
Only authorized Operator or Administrator roles may change autonomy levels. All changes require a mandatory written justification and are recorded in the immutable audit log with:
- Operator ID
- Previous and new autonomy level
- Timestamp (synchronized UTC)
- Reason for change
- Mission context
- Compliance mode (Civilian, Corporate, Government, DoD)
This design ensures alignment with DoD autonomy standards, NIST AI RMF governance principles, and enterprise safety requirements.
Validation and Research Posture
Simulation and synthetic benchmarks establish baseline behavior but plateau when stress conditions involve hardware-constrained dynamics, sustained network degradation, or audit integrity under prolonged failure injection.
Dedicated hardware validation is conducted separately to examine these limits under controlled conditions. See current validation research →
Continue Exploring
Interested in integrating ARIA into your systems? Contact us to discuss partnerships.